Technical and Organizational Measures
1 Introduction
This Technical and Organizational Measures (“TOM”) document covers the security and privacy controls for XUND’s suite of products.
With XUND’s products, you identify possible risks and causes for your symptoms using our database built from millions of medical publications powered by our artificial intelligence (AI). Based on self-reported data, XUND enables digital and automated interactions through relevant questions tailored to each stage in the patient journey. These features allow you to build customized health assistants for your patients.
This document provides a description of the main building blocks that contribute to the technical security and privacy of our suite of products and the organizational measures that surround the development and operation of the services. The target audience of the document is technicians, security-, and privacy experts who want to verify the details of the measures put in place by XUND.
2 Jurisdiction and locations
Headquarter's legal name, address, and jurisdiction:
XUND Solutions GmbH
Dorotheergasse 10/12a
1010 Vienna
Austria
XUND’s products and their databases are hosted in German data centers. Database backups and secondary disaster recovery sites are hosted in Dutch data centers. Diagnostic information and logs are also stored in Germany. A complete list of sub-processors and their locations is available at Sub-processor disclosure.
3 Service overview and architecture
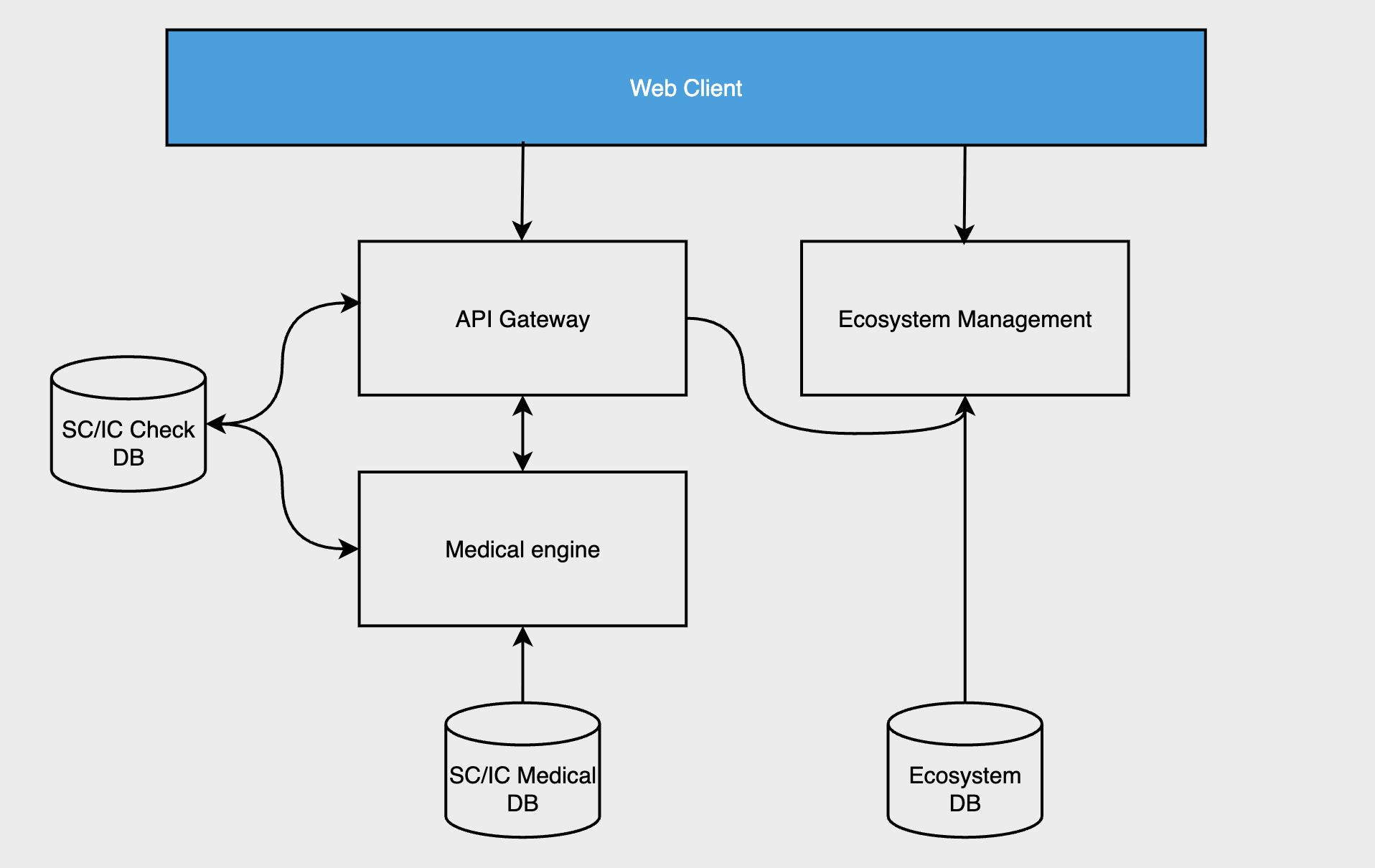
Our products consist of medical modules that cover the entire patient lifecycle and enable digital interactions from prevention to diagnosis and monitoring. They are standalone software without any physical components or accessories that supports layman users by providing them with trustworthy medical information in an intuitive and easy-to-understand way. XUND’s suite of products can be integrated into any frontend with an internet connection via API, SDK, and Web App interfaces.
Additionally to the medical modules, there are also add-on services that among other things also allow the management of the client settings and easier integration of the patient-facing UI. These web components share the same architectural setup as the rest of the service. Settings applied in the Client Hub constitute as instructions in regard to the processing of personal data.
XUND’s modules are provided as Software-as-a-Service (SaaS) solutions running at European data centers of a cloud provider. The products are running in a containerized environment where the hosts are partially managed by the cloud provider and partially by XUND.
We strive for data minimization and only collect personal data in the medical modules where it is absolutely necessary. For each patient interaction, a random check ID is generated that identifies questions and answers within a single session and produces a report. These check IDs are never mapped to any real profile information on the application backend.
3.1 Health Check
The Health Check is an application designed to process generic profile information, lifestyle, medical and family history as well as preexisting illness data provided by the user to generate an overall view of their health risks in one or more specific health topics. The purpose is to give recommendations and suggest potential examinations to the user to improve their health in the given topic(s).
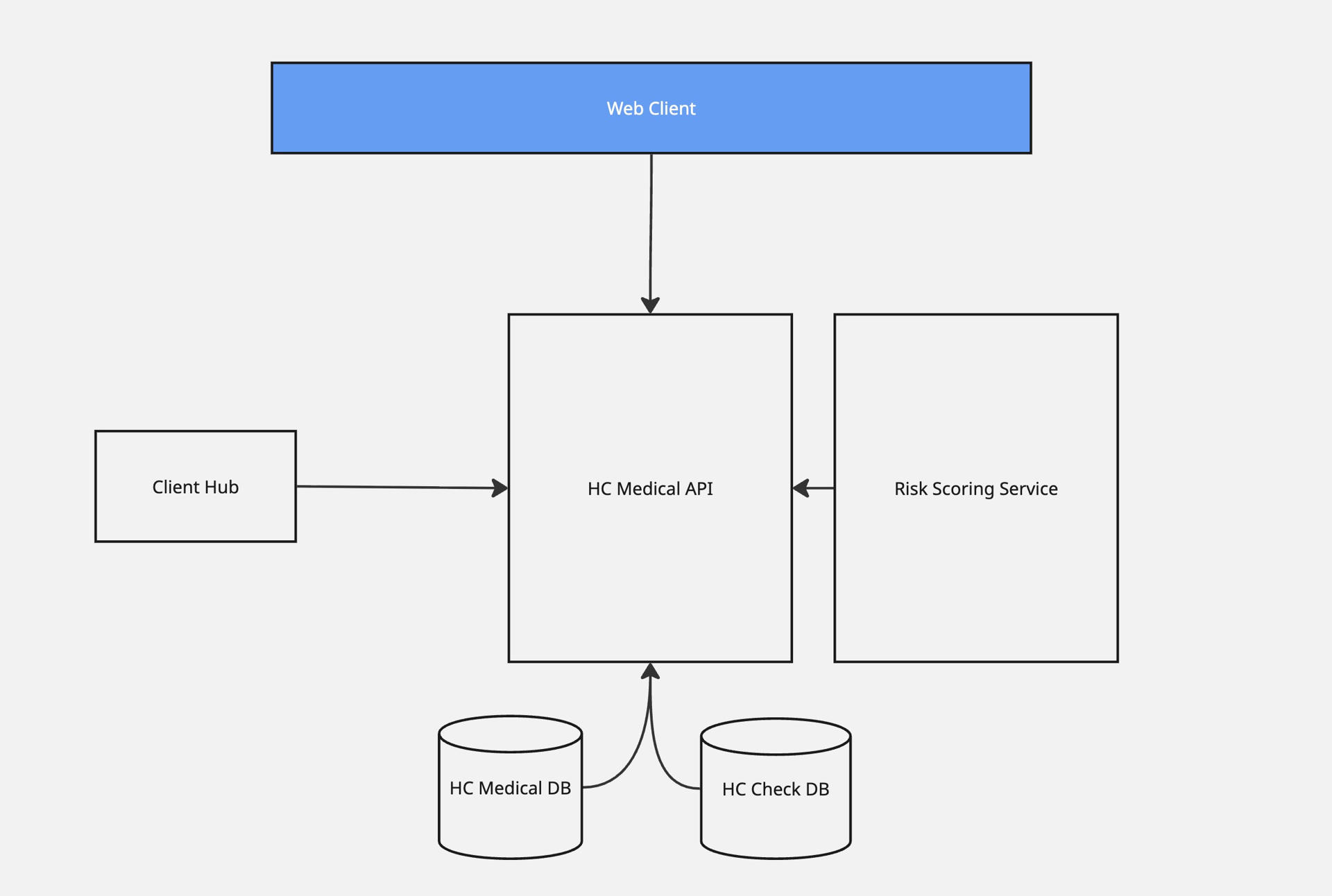
3.2 Symptom and Illness Check
The Symptom and Illness check is an application designed to process symptoms and generic profile information provided by the user to generate a preliminary assessment in diagnostic decisions. The purpose is to find potential evidence-based causes for the symptoms of the patient and empower them to identify relevant treatment pathways in the healthcare system.
4 Technical controls
We employ industry-standard technical security controls appropriate to the nature and scope of the service, designed to safeguard the service infrastructure and data residing therein. The technical and organizational measures described here constitute the measures referenced in the Data Processing Agreement that is part of the Terms of Service.
4.1 Access control
Logical access control procedures are in place, designed to prevent or mitigate the threat of unauthorized application access. Access for clients to the modules is provided based on API keys or pre-configured domain verification, whereas user authentication on client-facing UIs is done using a username and password combination with configurable two-factor authentication. XUND employees are granted minimum (or “least privilege”) access to specified XUND systems, applications, and devices as needed. Further, user privileges are segregated based on functional role and environment on a need-to-know basis.
4.2 Firewalls and network zones
XUND office networks and production networks are completely separated, with no VLAN connectivity between the two. Only required ports from application components are exposed within the service, and only containers containing the external interfaces are exposed to the Internet.
4.3 Data segregation
XUND operates a shared‑tenant SaaS architecture where customers share the same physical and virtual infrastructure, but all data is strictly separated through logical isolation. Each request carries a client identifier; application logic ensures that after client authentication queries are scoped so that a client can only access their own data. At the database level, we enforce client filtering via assigning each database row to a particular client. We perform regular risk analysis to identify threats such as cross‑tenant leakage, mis‑scoped queries or injection attacks, and selected these logical controls to preserve confidentiality and integrity. Access to raw database or unfiltered data is limited to a small set of privileged roles, all governed by change control and logging.
4.4 Physical security
XUND products are hosted at cloud providers leveraging European data centers where physical security and environmental controls were tested and certified according to ISO27001 and C5. These controls include:
- video surveillance and recording
- multi-factor authentication to highly sensitive areas
- heating, ventilation, and air conditioning temperature control
- fire suppression and smoke detectors
- uninterruptible power supply (“UPS”)
- continuous monitoring and alerting
- protections against common natural and man-made disasters, as required by the geography and location of the relevant data center
- scheduled maintenance and validation of all critical security and environmental controls
4.5 Business continuity and availability
The technical setup of the service allows dynamic scaling based on load and seamless handling of individual hardware errors. The suite of medical modules is hosted in data centers designed for zero downtime and is offered during contractually agreed service times with a yearly average availability of 99%, that is a maximum of 87 hours cumulative downtime a year.
In case of data center or database failures, we can, within 2 hours (Recovery Time Objective), relocate the service to a different location and serve traffic from there. In case of an incident, we can decide to move the service to a secondary site – which can already serve emergency operations and complete end user check flows – that will be running within 1 hour, and the service would be hosted there for at most 1 business day under emergency operations. In this state, the service will be able handle at least half the load of the primary site, but analytics and other auxiliary modules might not be available. Unless of a vis major, normal operation will be restored within 2 business days.
There are full backups created of the complete database every 24 hours (Recovery Point Objective) and kept within the same data center as well as at the geographically distant secondary location. Backups are encrypted at rest, and restoration capabilities are tested every 6 months.
4.6 Server updates
Our core services run in containers based on minimal images that are updated with the latest security patches on every release. The few services that run in traditional virtual machines are continuously monitored for applicable security updates and patched depending on risk or at least receive full patching once a quarter.
4.7 Encryption
XUND maintains a cryptographic standard that aligns with recommendations from industry groups, government publications, and other reputable standards groups. This standard is periodically reviewed, and selected technologies and ciphers may be updated in accordance with the assessed risk and market acceptance of new standards.
All network traffic flowing in and out of XUND’s server components, as well as in-between, is encrypted in transit.
4.8 Vulnerability management
Host-based vulnerability scanning is conducted daily. Static application vulnerability testing is run on every build, and penetration testing activities for targeted environments are performed periodically. These scanning and testing results are reported into monitoring tools, tracked in ticketing systems, and – as appropriate to the risk – remediation actions are taken. See more in the section on incident management.
4.9 Logging and altering
XUND logs all API requests and application errors with associated context for debugging purposes. Logs are forwarded to a central repository and cannot be modified. Only selected employees have access to these logs on a need-to-know basis. Any errors causing possible service interruption are monitored, and internal alerting notifies developers of the issue.
5 Organizational controls
5.1 Policies and procedures
XUND maintains a comprehensive set of security policies and procedures aligned with business goals, compliance programs, and overall corporate governance. These policies and procedures are periodically reviewed and updated as necessary to ensure ongoing compliance.
5.2 Standards compliance
During the development and operation of XUND’s medical modules, we comply with applicable security, data privacy, and other regulatory requirements. We and our products maintain compliance with the following certifications, external audit reports, and prominent regulations:
- ISO27001:2022 (issued by TÜV SÜD Landesgesellschaft Österreich on 1 Jul 2025, valid till 30 Jun 2028);
- scope is the design and development, production, operations and distribution of the medical software;
- all Annex A controls are applicable.
- ISO 13485:2016 (issued by TÜV SÜD Product Service GmbH on 30 Jan 2025, valid till 23 Feb 2028).
- Art 10 (9) of the Regulation (EU) 2017/745 on medical devices, classification class IIa (MDR) (certified by TÜV SÜD Product Service GmbH on 14 Jun 2023, valid till 22 Feb 2027)
- Regulation (EU) 2016/679 of the European Parliament and of the Council (GDPR)
-
Regulation (EU) 2024/1689 of the European Parliament and of the Council (AI Act)
5.3 Incident management
XUND maintains a Business Continuity Plan and an Incident Response Process defining response activities with associated timelines based on the results of a Business Impact Analysis. These also define reporting lines and management responsibilities. Incident notification - where incident here means an occurrence that results in the Service not functioning in accordance with the specifications thereof - can originate from internal monitoring, internal reports, through customer relation contacts as defined in service contracts, or external reports through our Vulnerability Disclosure page. Reported incidents are assigned a category according following criteria:
| Category | Initial Response Time | Description |
| Major - Service | 4 hours | Service is not available for use, key functionalities are not available, or security risks to end users is critical, impact of Incident is significant |
| Major - Security | 24 hours | Service is available and not impaired, but a high security risk to end users exists |
| Medium | 24 hours | Service is available, but in an impaired fashion, impact of Incident is high |
| Minor | 48 hours | Service or parts of it are slightly impaired, impact of Incident is low |
XUND will endeavor to prioritize incoming incidents during contractual service time as soon as possible based on the initial category. As part of prioritization, the category may be reevaluated by XUND in agreement with the client if the context of the incident changes for reasons such as:
- the category has been set wrongly not matching the classification above;
- a workaround had been emplaced which reduces or eliminates the problem;
- the fault has been cleared;
- the problem disappeared by its own.
After processing the incident report, based on the final category, XUND will use best effort to resolve the incident within below timelines.
| Category | Recovery Time |
| Major - Service | 1 business day |
| Major - Security | 20 business days* |
| Medium | 6 business days |
| Minor | 20 business days |
In case XUND fails to meet its availability (as defined in section 5.5 and calculated on a yearly basis as an average availability) or the above Recovery Times multiple times in consecutive months, the client is entitled to Service Level Credits. Service Level Credits are calculated monthly by XUND and deducted from the service fee of the next month. The contract between the client and XUND will contain these support level clauses and can also be replaced with other client specific guarantees.
*Unlike service outages (where the focus is on rapid restoration), security incidents often require thorough investigation and safe restoration which can take significantly more time.
5.4 Government inquires
To date, XUND has not received any government enquiries or legal requests for client data. However, we have established procedures to ensure compliance with applicable laws and to protect the interests of our clients should such a situation arise.
Upon receiving a government enquiry, details of the sender, their authority, and the communication channel used are documented. The request is formally logged to ensure traceability. The enquiry is then reviewed together with our respective legal counsels to confirm its legal validity, taking into account jurisdiction, scope, and any country-specific laws. Only requests with a clear legal basis will be processed further. If required by the contract and to the extent legally permitted, we promptly inform the affected customer about the enquiry and provide all relevant details.
After confirmation of validity, the specific data requested by the authorities is reviewed and identified in our systems. The scope of the request is then evaluated to ensure that only strictly necessary and relevant data is considered. The review will also determine whether the requested data is available, accessible, and if encrypted, whether XUND has the technical means to access or decrypt it. Any limitations on data accessibility are documented.
In case client notification was permitted, we provide clients reasonable support in accordance with legal and contractual obligations to object to the enquiry. Based on the legal review and client input, a formal response to the enquiry will be prepared. This response will either provide the requested information or justify the rejection if there are valid grounds for it.
An audit trail is maintained for all actions, communications, and decisions relating to the enquiry. This ensures compliance and allows for future review if necessary.
5.5 Application security
The application security program at XUND is based on a formal Secure Development Process that defines minimally required security activities to be done before releases. The program is based on providing secure development training to all engineers and leveraging practices such as design and code reviews, threat modeling, static analysis, software composition analysis, and external vulnerability and application scans.
5.6 Personnel security
Background checks to the extent admissible and proportionate to the role are being done for all new hires prior to employment. Employees need to go through a formal onboarding and offboarding process respective to their employment status, where records of completion are maintained internally. Access to systems is reviewed on a yearly basis, ensuring employees only have privileges in systems they actually need for their daily tasks.
5.7 Security awareness and employee training
All new hires need to go through initial security awareness training and accept the company's internal playbook containing relevant security obligations. Yearly follow-up training and awareness exercises are held for all employees, and every two months, there is an internal employee newsletter containing relevant information on recent security threats. Engineers receive additional secure development training on an ongoing basis.
6 Use of sub-processors
As part of providing the service, we are using the services of suppliers and service providers (collectively sub-processors) with whom we might share personal data as part of the services. XUND provides an up-to-date list of its sub-processors available on its website at Sub-processor disclosure. XUND will notify clients in case there are any changes in the list or the way sub-processors are involved in provisioning the service.
All sub-processors need to go through a defined vendor evaluation process before being introduced, including aspects of quality, security, and privacy. All sub-processors are regularly being re-evaluated to ensure the ongoing quality of the used services. All sub-processors need to have a signed statement of work, confidentiality agreement, and data processing agreement with provisions compatible with those signed by XUND towards its clients.
In selecting sub-processors, there is a large emphasis put on ensuring the high level of privacy of their services, as XUND commits itself to. Sub-processors are selected based on the privacy regulations applicable at the headquarters of the company, hosting locations leveraged, and additional technical and organizational privacy controls provided. Providers from countries without adequacy decisions from the European Commission are only used where appropriate further safeguards have been put in place.
7 Contacting XUND
Clients can contact us for privacy-related inquiries at privacy@xund.ai or through their respective Partnership Manager.
Version v1.0, updated on November 18, 2025.